
Years ago, cybersecurity for the average person was hoping to avoid viruses after a download or installing security software. Now that digital data is everywhere, it’s become an incredibly difficult task to keep track of digital security. Because technology is constantly evolving, the spectrum of unethical violations and data breaches expands infinitely. How can anyone assess the full scope of the risk?
Privacy and Data
It wasn’t long ago that people were unknowingly recorded by their smart home device. We could all be recorded or filmed and never know it happened, even though we didn’t consent. How could the company drop the ball like that? Many companies have more data than they can handle which becomes a security risk. California is paving the way for a lot of issues in tech and connectivity, so it’s not surprising that the golden state became the first to pass an IoT law requiring smart home tech and the responsible companies to create better security features to prevent unauthorized access. In order for companies to remain in control of security, they have to scour every corner internally first.
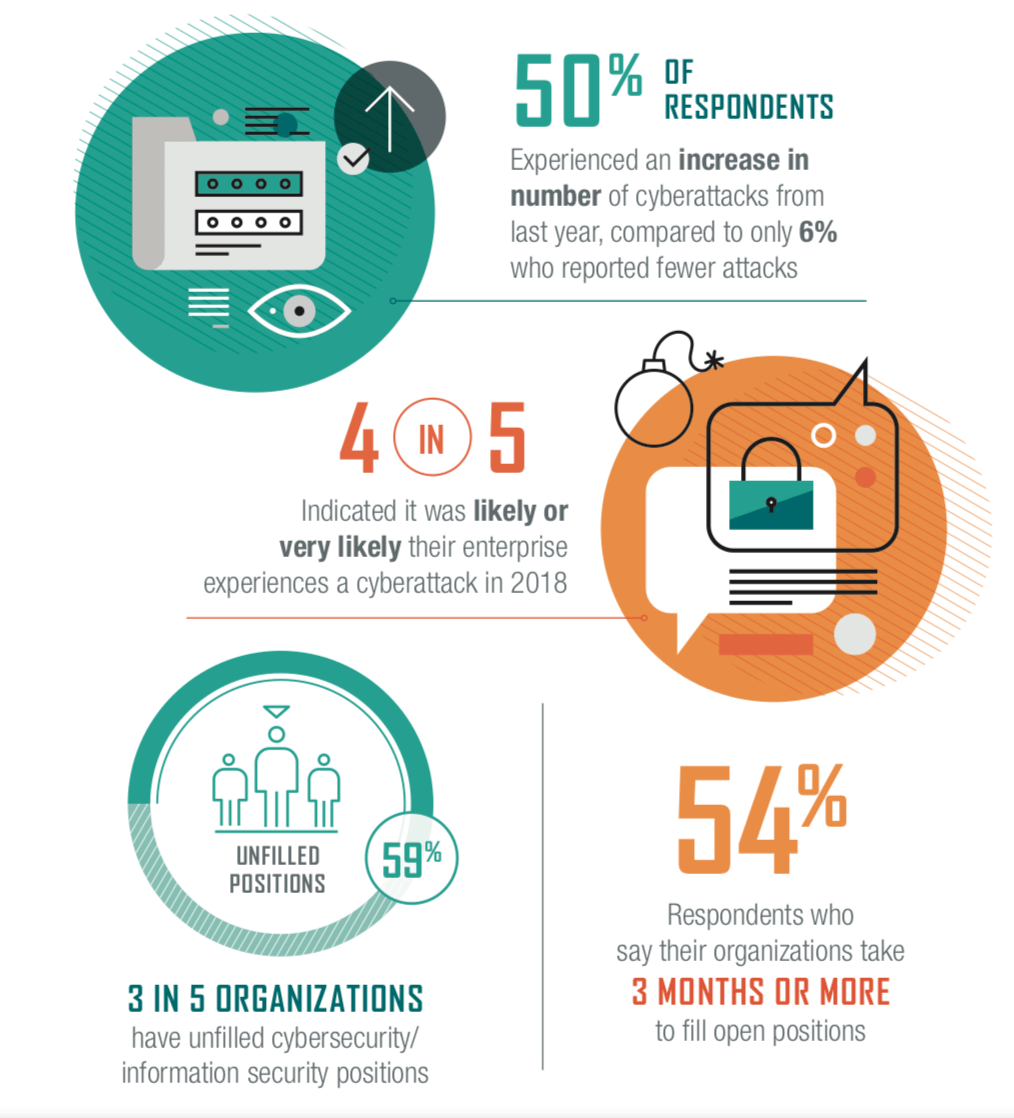 Consider this, is it a violation that companies don’t make timely reports of data breaches, even though millions of customers are compromised? It definitely is, but why aren’t they doing anything about it? These data breaches frequently happen because of the volume and complexity of data. When you can’t understand the data, you can’t protect it. If it’s difficult to understand, do something with the data. Many companies don’t even have enough manpower or resources to begin analyzing cybersecurity, let alone all the data they collect. If you don’t know how to start, start with data visualization. In every case, the data will be analyzed but requires a form that’s easier to understand. It doesn’t matter if it’s a dashboard or full report, security needs usable data, and it’s not usable if you don’t know what it means.
Consider this, is it a violation that companies don’t make timely reports of data breaches, even though millions of customers are compromised? It definitely is, but why aren’t they doing anything about it? These data breaches frequently happen because of the volume and complexity of data. When you can’t understand the data, you can’t protect it. If it’s difficult to understand, do something with the data. Many companies don’t even have enough manpower or resources to begin analyzing cybersecurity, let alone all the data they collect. If you don’t know how to start, start with data visualization. In every case, the data will be analyzed but requires a form that’s easier to understand. It doesn’t matter if it’s a dashboard or full report, security needs usable data, and it’s not usable if you don’t know what it means.
The ethics of data violations
Privacy violations aren’t always so obvious, even when the data is well-organized. Take this for example, a digital platform that helps employers keep track of freelance work and offers a tracker that doubles as a frightening nightmare for freelancers. The tracking feature monitors everything from keystrokes to mouse movement and will even take photos (via webcam access) of freelancers. Even though the platform is seemingly “secure,” it’s incredibly invasive. Why all that data? Is this form of data collection dangerous? What does the data do for the freelancers? How many people feel uncomfortable? These questions provide crucial insights into customer base, but isn’t always considered. Customer data is critical to livelihood and that data needs to be considered too.
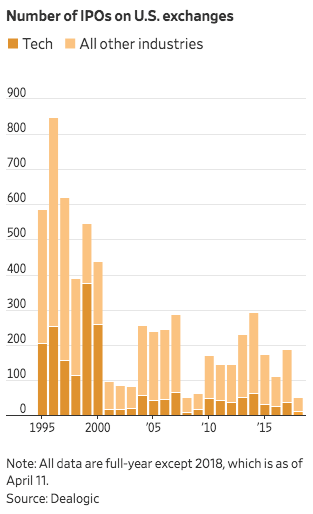 The security of consumers is a strong indicator of IPO success. Even a company as strong and powerful as Facebook saw drastic falls in IPO after security breaches were reported. Don’t think it’s that important? Just imagine how much of your data has been risked for investments.
The security of consumers is a strong indicator of IPO success. Even a company as strong and powerful as Facebook saw drastic falls in IPO after security breaches were reported. Don’t think it’s that important? Just imagine how much of your data has been risked for investments.
What now?
Data visualization is the one stop shop that can give you the power to regain control over your data. It can even be used for training to reduce future risk so why are so many businesses letting their and customer livelihood suffer? Make it an issue, visualize it, scrutinize the analysis, and do something about that data. Even tech giants are leading by example, prompting a closer look at cybersecurity so people can ask, “How safe is my data?”
